
Enhancing 4G Router Security for a Safer Network
As 4G LTE technology continues to expand, cybersecurity becomes more important, and the security of 4G routers is becoming more important as they provide high-speed connectivity and support a myriad of applications. 4G routers are susceptible to a variety of security threats that can compromise individual users and large networks, and how to enhance the security of 4G routers and create a more secure network has become a top priority.

1. 4G Industrial Router Network Security Features
Various features and policies designed to protect the integrity, confidentiality, and availability of data and resources within a network. Here are some of the key cybersecurity features:
Firewalls: Firewalls are an important part of network security, acting as a barrier between trusted internal networks and untrusted external networks. They inspect incoming and outgoing traffic based on predefined security rules to block unauthorized access and threats, such as malware and application-layer attacks.
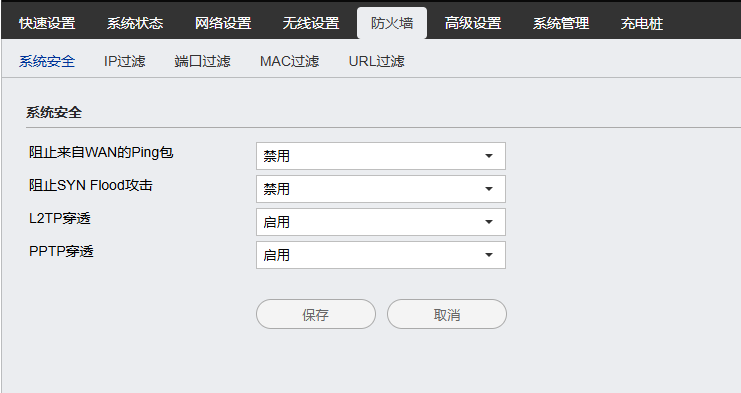
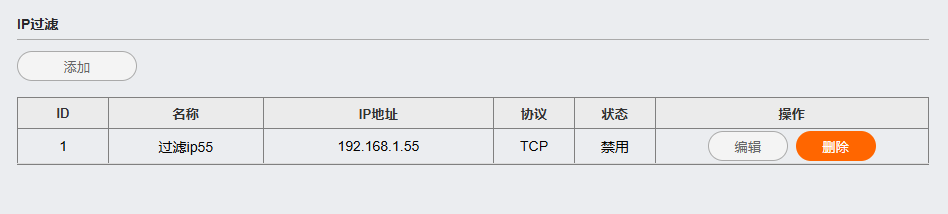
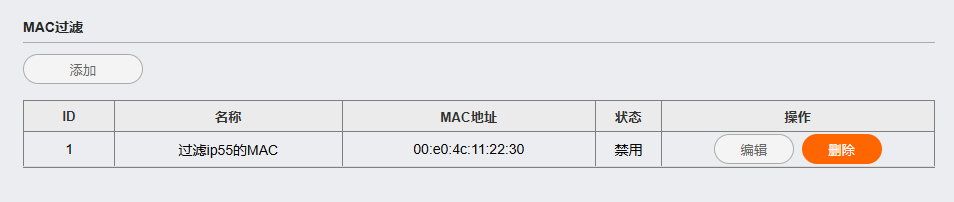
Access control: The access control mechanism restricts network access for authorized users and devices. This feature can be enhanced with IP filtering, MAC filtering policies to ensure that only licensed entities can access the router network.
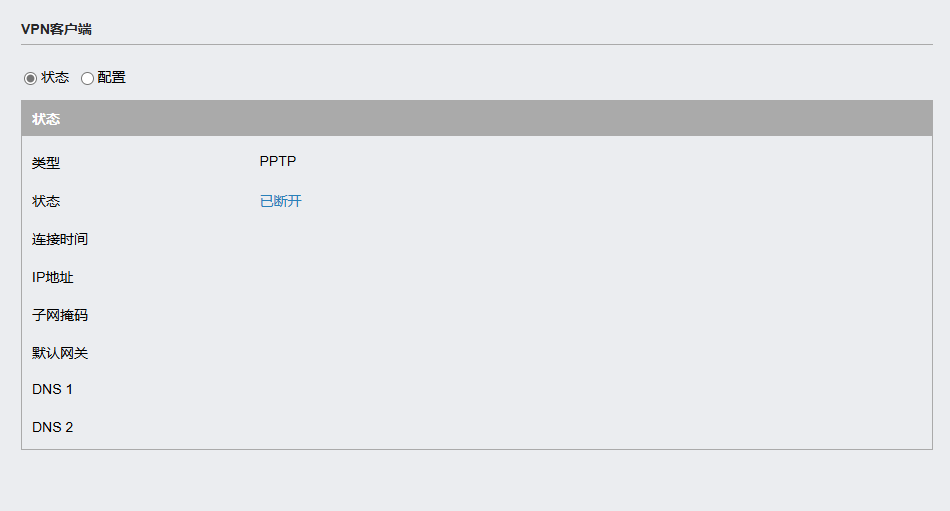
Virtual Private Network (VPN): Supports VPN connections and provides a secure communication channel on the public network by encrypting data to ensure privacy and integrity. At the same time, you can view the VPN connection status, record the connection time, etc.
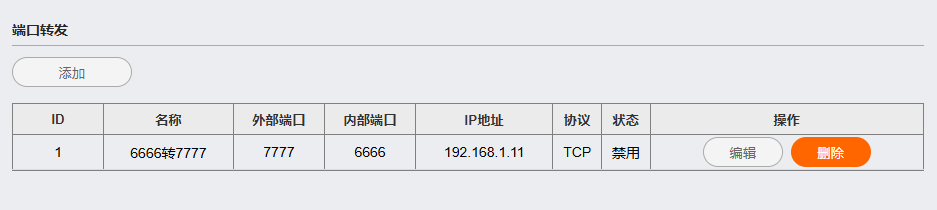
Port forwarding: Port forwarding as a NAT implementation, often referred to as port address translation (PAT), allows external devices to access services on a private network, directing incoming traffic on a specific port to a specified device within the local network by mapping the router’s public IP address and port number to the private IP address and port of the internal service. With port forwarding, networks can maintain security by hiding internal IP addresses while allowing controlled access to specific services from the outside world.
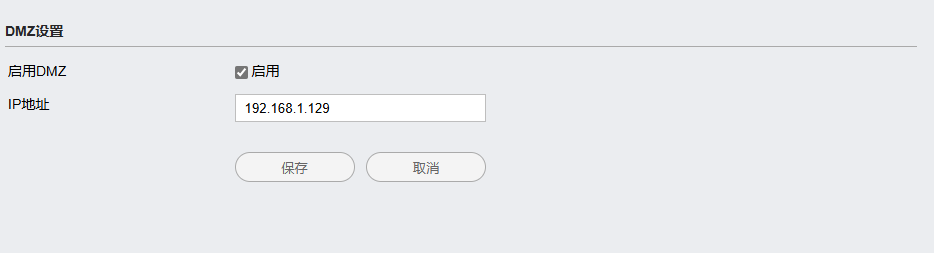
The Quarantine Zone (DMZ) : DMZ configuration creates an intermediate zone between the internal network and the external network, such as the Internet. This area is used to place equipment that needs to provide external services, such as web servers, mail servers, etc. It exposes certain servers to external network access while securing the internal network. By placing these servers in a DMZ, even if they are attacked, the attacker cannot directly enter the internal network.
Intrusion detection and prevention systems (IDPS): These systems monitor network traffic for suspicious activity and can alert administrators (IDS) or proactively block threats (IPS). They are essential for defending against attacks such as brute force attempts and DDoS attacks.
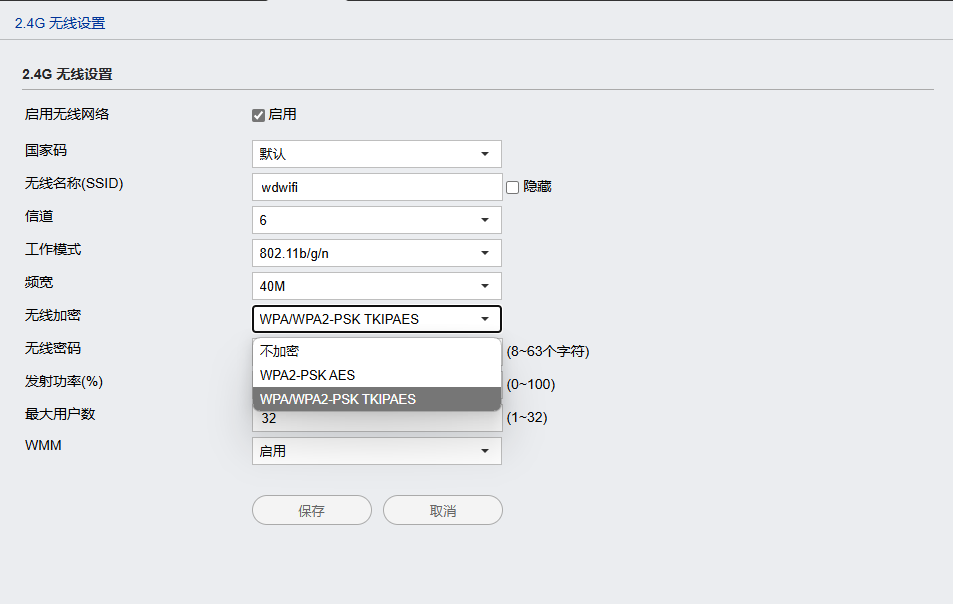
Encryption: WIS901 4G router enables the router to significantly improve the security of the network and prevent hacker attacks and data leakage by using strong encryption protocols such as WPA3. Require users to authenticate, verify the identity of the sender and receiver, and ensure that the data is coming from a legitimate source.
Overall, cybersecurity is a comprehensive approach, and cybersecurity protection for the WIS901 4G router involves multiple layers of defense and a variety of tools and techniques to protect the network from ever-changing cyber threats.
2. Remote management and Data monitoring
WIS901 4G industrial router supports remote management and monitoring to achieve efficient operation and maintenance of 4G routers. This feature enables real-time monitoring of device status, troubleshooting, and timely problem resolution, which is critical for maintaining network security and performance.

A virtual private network (VPN) creates an encrypted tunnel for secure remote access. VPNs enable secure remote management and monitoring of networks, protecting data transmitted over public networks from unauthorized access.
VPN and port forwarding: Remote access to a 4G router is typically achieved through a VPN or port forwarding. However, traditional methods such as port forwarding are not always feasible due to carrier-grade NAT (CGNAT) allocation of dynamic private IP addresses. Instead, a VPN tunnel can be established, and the 4G router acts as a client for encrypted communication.
Remote configuration and support: The WIS901 4G routers are all pre-configured for remote management, allowing users to access and modify settings through an online platform. Makes it simple and efficient to manage routers deployed in hard-to-reach areas or applications that require frequent configuration changes.
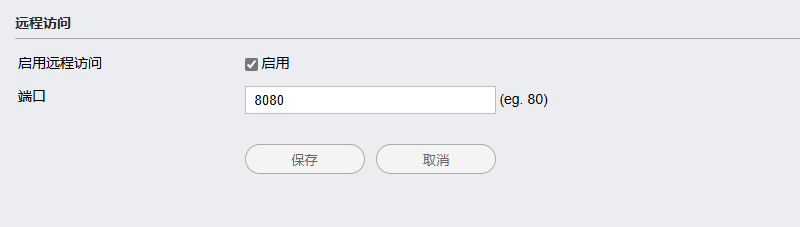
Overall, the WIS901 4G router offers a powerful solution for remote management and monitoring, making it ideal for a wide range of applications, from industrial automation to smart building management. These capabilities ensure that the network remains secure, efficient, and responsive to changing operational needs.
3. Real-time monitoring and security audits
Real-time monitoring of faults and safety
The real-time monitoring capabilities of 4G routers play a vital role in enhancing network security and operational efficiency for a wide range of applications. The WIS901 4G router includes a fault detection feature that alerts administrators to problems in real-time. This allows for timely troubleshooting and resolution, minimizing downtime and maintaining network stability. Real-time monitoring enables continuous observation and management of data and processes, enabling immediate detection and response to any anomalies or security threats.
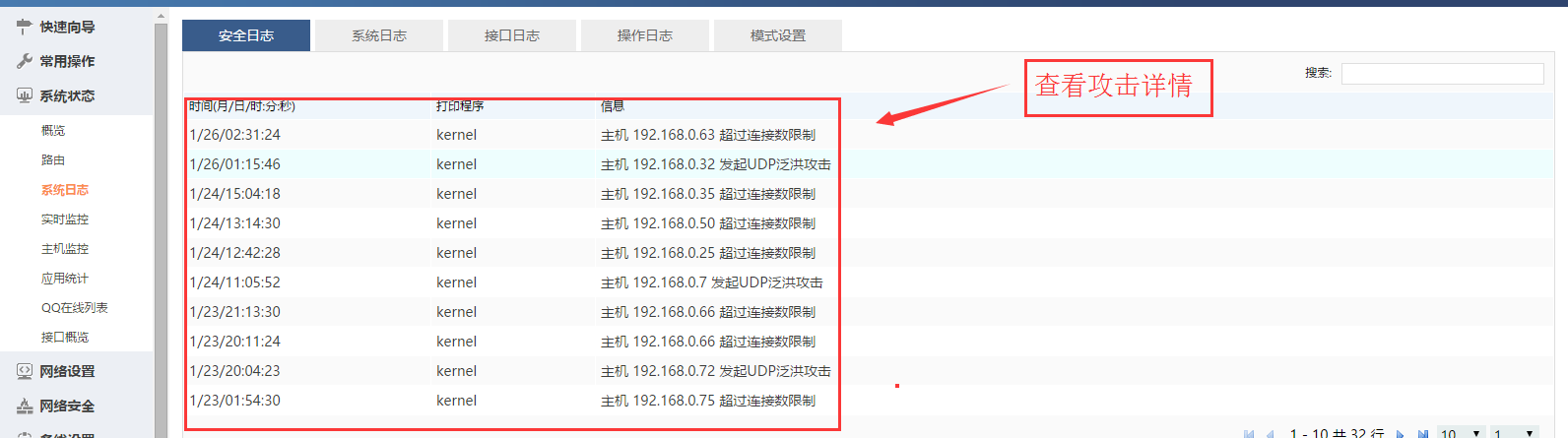
At the same time, the WIS901 4G router has detailed logging capabilities that enable administrators to track network activity, identify potential threats, and respond to security incidents in a timely manner.
Security audits
The WIS901 4G router undergoes regular security audits, analyzing logs to identify potential vulnerabilities or violations. By reviewing security logs, administrators can spot unusual activity or access attempts that may indicate a security issue. Audits help take corrective actions, such as updating security protocols, patching vulnerabilities, and improving access controls.
Overall, the WIS901 4G router provides a powerful solution for real-time monitoring and security, making it an essential part of industrial applications. Their security features help protect against cyber threats and ensure reliable, secure data transfer.
4.Firmware update and patch management
Firmware updates
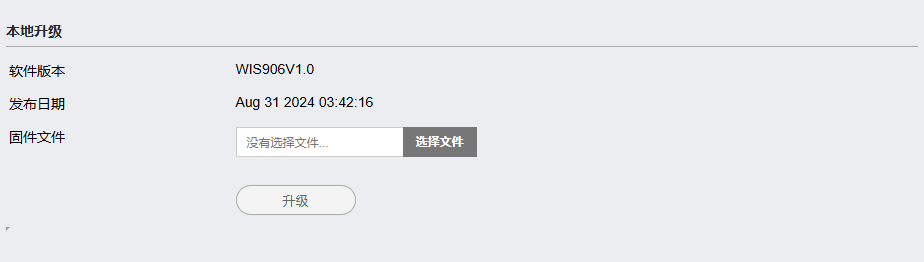
The system supports manual firmware updates for 4G routers, users only need to download the latest firmware version and install it through the router’s web interface. Firmware updates are essential to maintain the performance of the router, add new features, and most importantly, enhance network security, by keeping the router firmware updated, users can protect their network from evolving cyber threats, ensuring data security and network reliability.
Security patch management
The WIS901 4G router manages security patches to maintain router security by addressing known vulnerabilities.
Periodic vulnerability assessment: Regularly assess vulnerabilities to assess whether the device has vulnerabilities. When a vulnerability is discovered, a security patch is developed to address it. These patches are essential to prevent attackers from exploiting.
Patch deployment: After the security patch is released, it will be provided to users through the official website of the router. Administrators can configure the router to apply these patches automatically or manually approve them after testing in a controlled environment.
Compliance and reporting: Regular patch management ensures compliance with industry standards and regulations. Many organizations need to document patch management activities as part of their security strategy. The WIS901 4G router provides this document for auditing and demonstrating commitment to maintaining a secure network environment.
Testing and validation: Before deploying patches, especially in industrial environments, they often need to be tested in controlled settings to ensure compatibility with existing systems and applications. This step helps prevent potential disruptions caused by patching.
Overall, a combination of firmware updates and careful security patch management ensures that the WIS901 4G router remains secure and able to defend against emerging threats.

Summary
The WIS901 4G router provides a secure and reliable connection and protects the network from a wide range of threats by implementing comprehensive cybersecurity measures, including strong hardware and software security and effective risk management,Enhancing 4G Router Security for a Safer Network.