
Block SYN Flood attacks
Introduction to SYN Flood attacks
A SYN Flood attack is a type of denial-of-service (DoS) attack where an attacker sends numerous SYN requests to a target server, overwhelming it with half-open connections. This consumes server resources, preventing legitimate users from establishing connections. Such attacks disrupt services and degrade network performance, making them common in cyberattacks.

The impact of SYN Flood attacks on network security can be severe:
• Resource Exhaustion: The server’s resources, such as memory and processing power, become overwhelmed by the large number of half-open connections, making it unable to handle legitimate requests.
• Service Disruption: As the server struggles to manage the volume of SYN requests, legitimate users may experience increased latency or complete service unavailability.
• Network Congestion: Excessive traffic can lead to network congestion, further degrading performance and reliability.
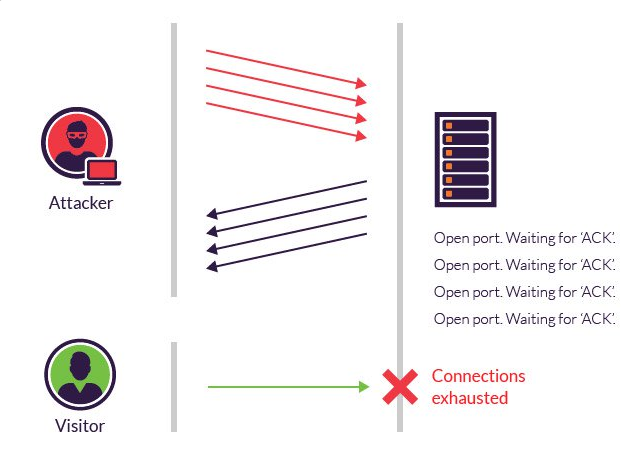
How 4G routers detect and mitigate SYN Flood attacks
4G routers can play a vital role in detecting and mitigating SYN Flood attacks.
How 4G routers detect SYN Flood attacks
Traffic Monitoring:The 4G router includes the ability to monitor network traffic, detecting the presence of a SYN Flood attack by tracking the number of SYN packets and identifying if traffic spikes deviate from the peak of normal traffic patterns.
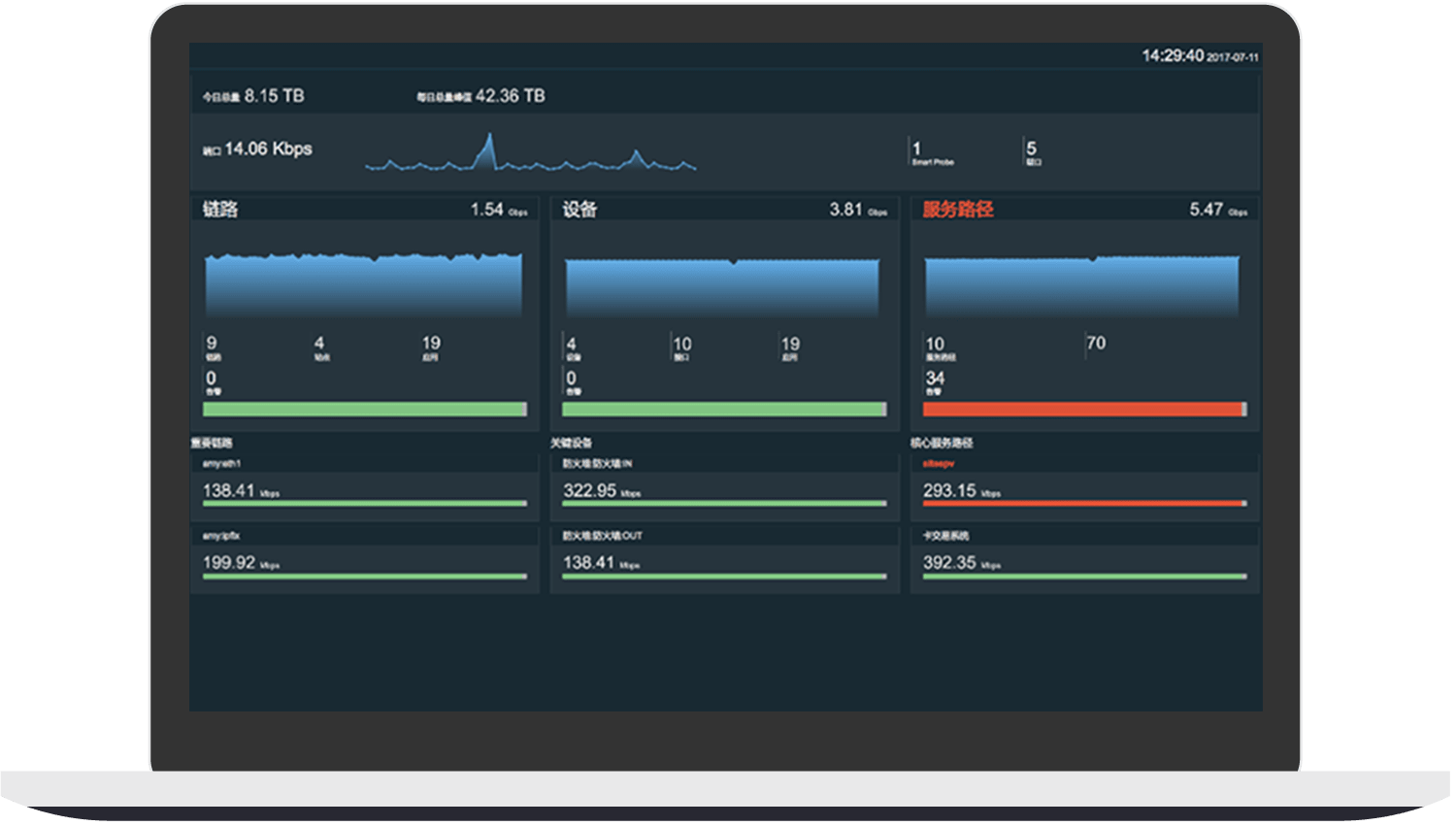
Anomaly Detection System:4G routers are equipped with behavior-based anomaly detection systems that can identify anomalous traffic patterns, such as a sudden increase in semi-open connections, which is characteristic of SYN Flood attacks, which are labeled as SYN Flood attacks.
How 4G routers mitigate SYN Flood attacks
Rate Limiting:By limiting the rate at which incoming connections can be made, the router can prevent its resources from being overwhelmed by a large number of SYN packets.
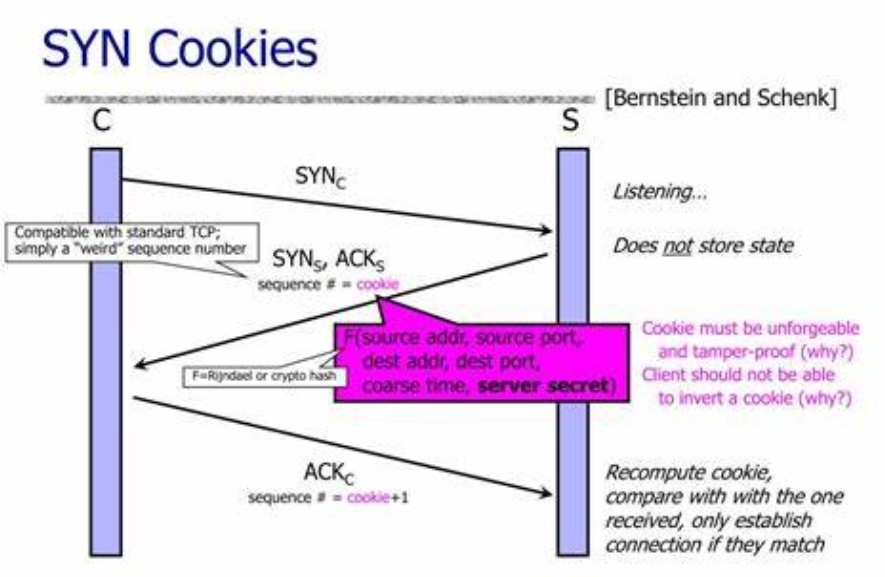
SYN Cookies:During a SYN Flood, where an attacker sends a large number of SYN requests to a server without completing a TCP handshake, overwhelming server resources, the SYN cookie helps by encoding the connection information into the TCP sequence number of the SYN-ACK packet. This allows the server to defer resource allocation until the final ACK is received, ensuring that only legitimate connections consume resources. This technology enhances the server’s ability to defend against such attacks by preserving resources and maintaining service availability.
Firewall:Configure the firewall to block SYN Flood attacks and block detected SYN Flood attack IPs and traffic

Through these technologies, 4G routers can effectively detect and mitigate SYN Flood attacks and ensure network stability and security. These measures help maintain service availability and prevent potential disruptions caused by such attacks.
Test the SYN Flood protection function of the 4G router
The purpose of this test is to evaluate the effectiveness of the 4G router’s SYN Flood protection capabilities. By testing a router’s ability to detect and mitigate SYN Flood attacks, we can assess its impact on network performance and ensure the security of the network.
1. Test environment:
Hardware and Software Requirements
4G router: Huizhi Technology’s 4G router
Attack tool: hping3
Test equipment: attack aircraft: ubuntu 192.168.225.73 target aircraft: win11 192.168.225.95

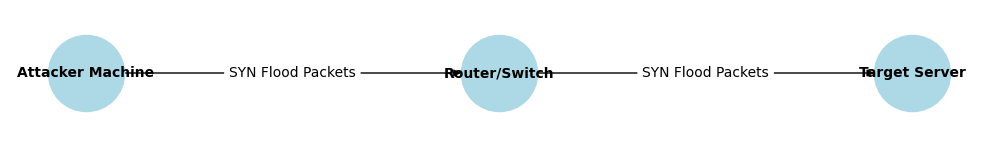
Network topology
Router setup: Huizhi Technology’s 4G router is wired to the Internet and local network through the WAN port.
Attack device: An attack aircraft running hping3 to simulate a SYN Flood attack.
Target device: The target machine is connected to the LAN port of Huizhi Technology’s 4G router through the Ethernet port
2. Test scenario:
Normal conditions: Measure network performance without any attacks.
Low-intensity attacks: Measure network performance with a moderate number of SYN packets simulating a SYN flood.
High-intensity attack: Increase the number of SYN packets to test the router’s ability to resist high-intensity attacks.
Long-term attacks: Continuous SYN Flooding over an extended period of time to assess the long-term performance of the router.
3. Test steps and their results:
1. Normal Conditions
If a SYN Flood attack is not launched, observe the CPU and memory usage through the router system website, and use the ping www.baidu.com command to view the network packet loss and connection success rate.
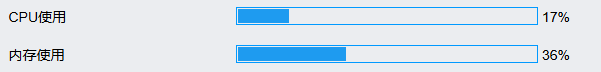
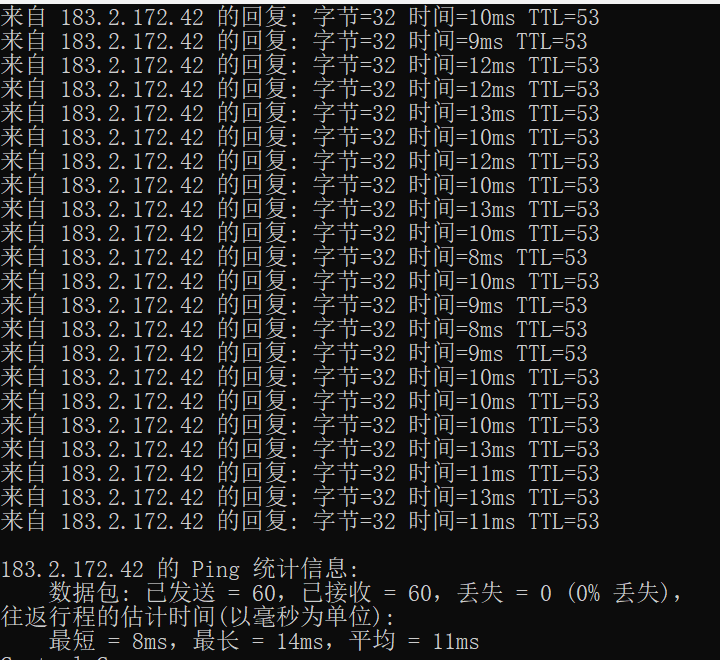
When the router firewall is disabled to prevent SYN Flood attacks, and the attacker does not launch a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are asfollows:
When the router firewall is enabled to prevent SYN flood attacks, and the attacker does not launch a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:


2. Low Intensity Attack
Run the following command on the attacking device to start a low-intensity SYN Flood: sudo hping3 -S -i u500 -p 80 –rand-source 192.168.225.95
Observe CPU and memory usage through the router system website, and use the ping www.baidu.com command to view network packet loss and connection success rate.
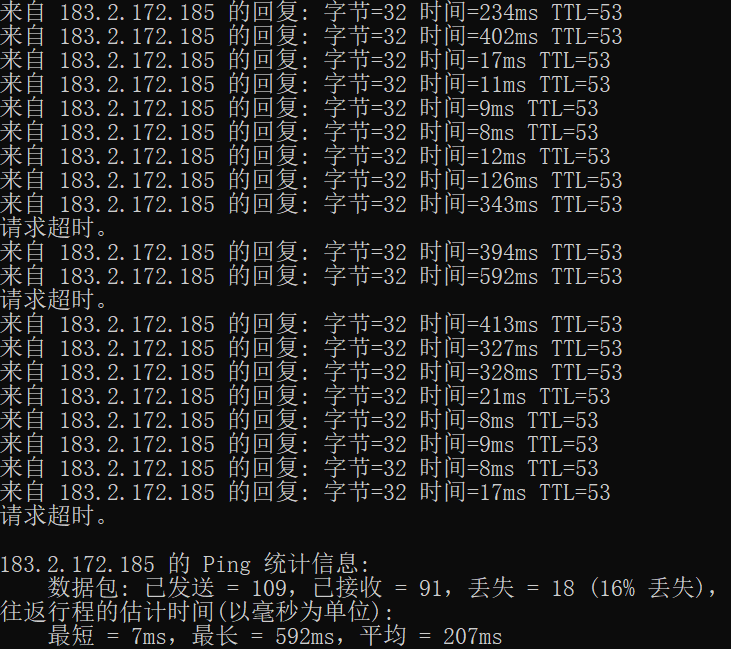
When the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:

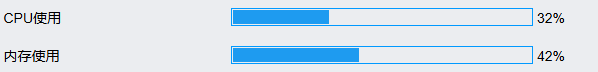
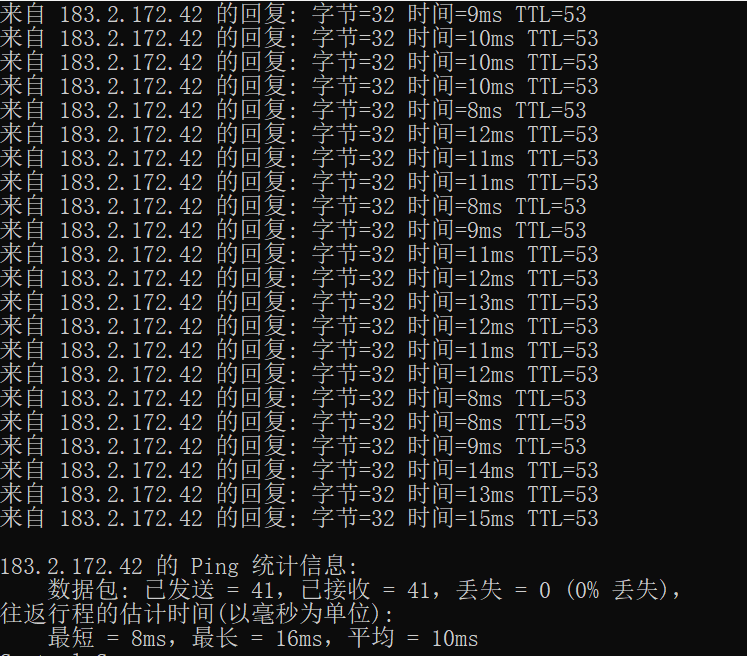
When the router firewall is enabled to block SYN Flood attacks, when the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:
3. High-intensity attack
Increase the packet rate in the hping3 command on the attack device to simulate a high-intensity attack: sudo hping3 -S -i u200 -p 80 –rand-source 192.168.225.95
Observe CPU and memory usage through the router system website, and use the ping www.baidu.com command to view network packet loss and connection success rate.
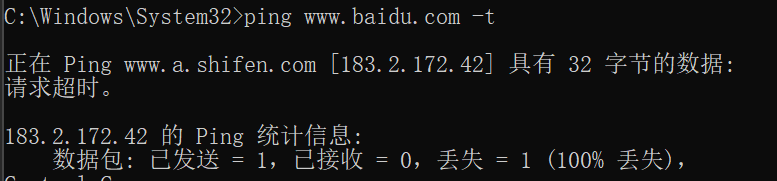
When the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:

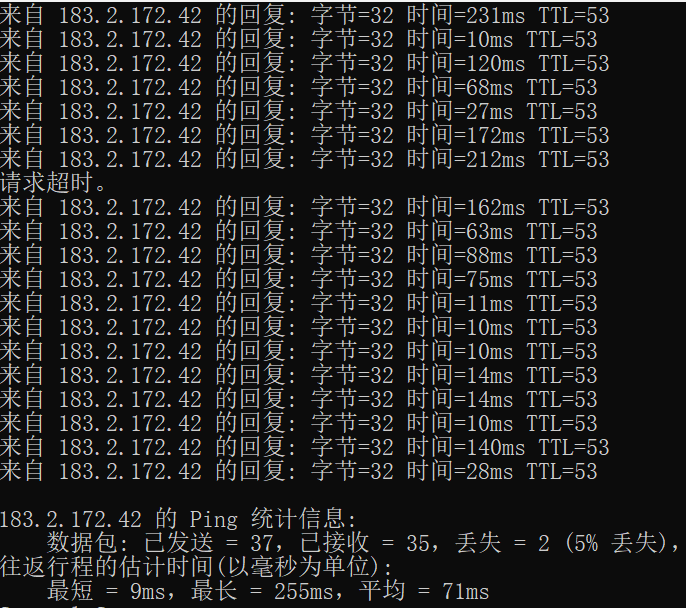
When the router firewall is enabled to block SYN Flood attacks, when the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:

4. Long Attack
Maintain a high-intensity attack (30 minutes) on the attack device for a long time.
Observe CPU and memory usage through the router system website, view network packet loss and connection success rate through ping www.baidu.com commands, and continuously monitor network performance indicators and router responses.
When the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:

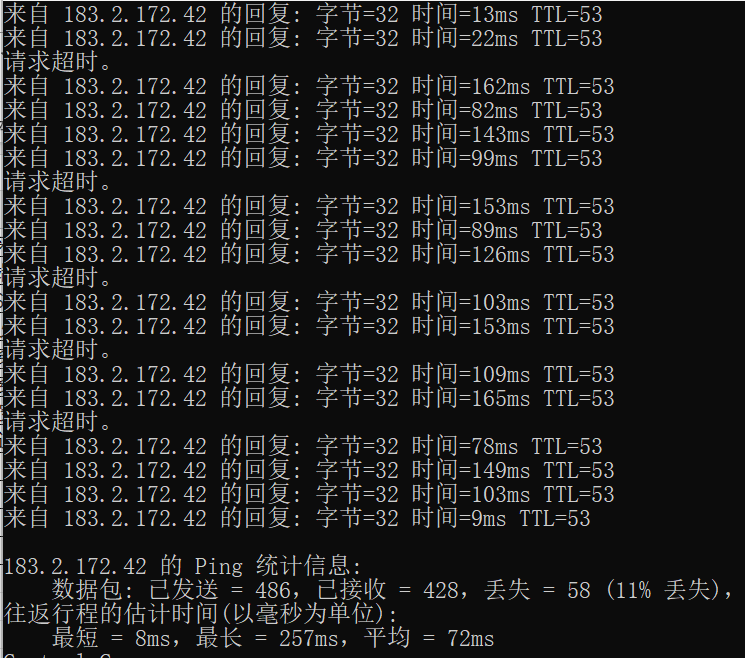
When the router firewall is enabled to block SYN Flood attacks, when the attacker launches a SYN Flood attack, check the router CPU and memory usage, packet loss, and connection success rate, and the results are as follows:

Results & Analysis
Data display:
For clarity, organize the collected data into a table:
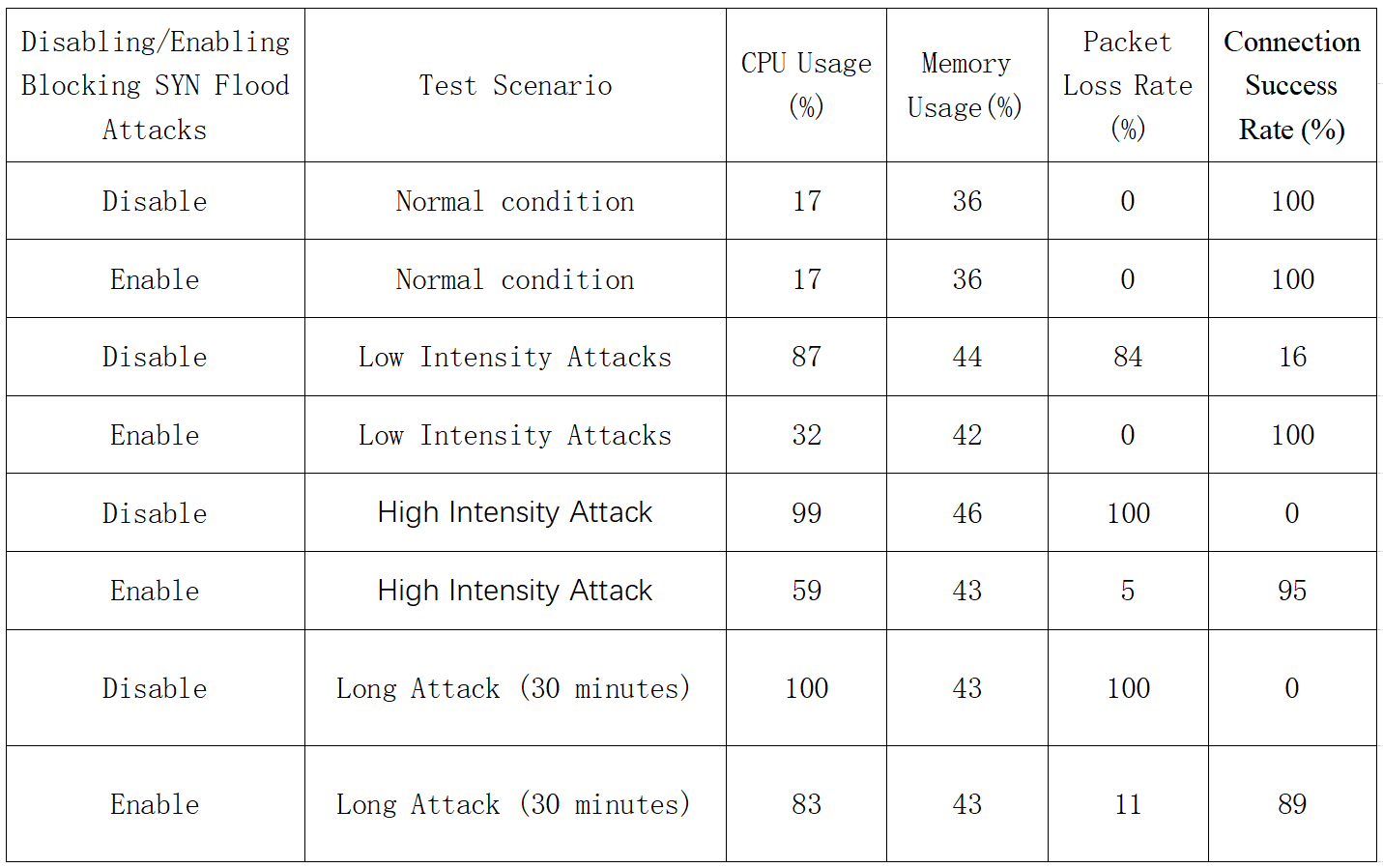
Analyse
Normal Conditions:
CPU and memory usage: Both remain low (17% CPU, 36% memory) regardless of whether SYN Flood protection is enabled or disabled.
Packet loss and connection success rate: There is no packet loss in both scenarios, and the connection success rate is 100%.
Low Intensity Attack:
Unprotected: CPU usage spikes to 87%, packet loss is 84%, and connection success is only 16%.
Protected: CPU usage drops to 32%, no packet loss, and a 100% connection success rate.
High Intensity Attack:
Unprotected: CPU usage is almost 99%, packet loss is 100%, and connection success is 0%.
With protection: CPU usage is reduced to 59%, packet loss is only 5%, and connection success rate is as high as 95%.
Long Attack(30 minutes):
Unprotected: CPU usage reaches 100%, packet loss is 100%, and connection success is 0%.
Protected: CPU usage is 83%, packet loss is 11%, and connection success is 89%.
Effectiveness of SYN Flood Protection: Enabling SYN Flood Protection significantly reduces CPU usage and packet loss while maintaining a high connection success rate, even under high-intensity and prolonged attacks.
Service Availability: Huizhi Technology’s 4G router effectively maintains service availability with SYN Flood protection enabled, demonstrating a strong ability to mitigate the impact of SYN Flood attacks.

Summary
According to the test results, it can be observed that the attacker’s computer sends SYN Flood packets to the target server through the 4G router, enabling SYN Flood protection on the 4G router reduces CPU usage, minimizes packet loss and maintains a high connection success rate in the event of an attack, thereby significantly enhancing the resilience of the network, this protection ensures that legitimate traffic is handled efficiently, preventing service interruptions and maintaining network performance. It can be seen that Huizhi Technology’s 4G router can mitigate the impact of SYN Flood attacks and provide a stable and secure network environment.